Security Posture Score
Track your organization's overall security posture with real-time scoring and trend analysis
Know where your sensitive data lives with continuous scanning and real-time visibility across your entire IT ecosystem
Comprehensive data security posture management across your infrastructure
Identify and classify sensitive data across cloud, databases, and endpoints
Focus on high-risk exposures using AI-powered risk scoring
Detect unprotected cloud storage, open databases, and excessive permissions
Uncover unknown and orphaned data across cloud and on-prem environments.
Detect changes in data security posture in real-time
Get actionable steps to fix security gaps and misconfigurations
Simplifying audits and demonstrating compliance across your organization
European Union General Data Protection Regulation compliance reporting
Health Insurance Portability and Accountability Act compliance reporting
California Consumer Privacy Act compliance reporting
Service Organization Control 2 security and compliance standards
A streamlined approach to securing your organization's data assets
Automated scanning of your entire IT infrastructure to find sensitive data
AI-powered risk assessment and intelligent data classification
Risk-based prioritization of security gaps and exposures
Guided remediation with continuous posture monitoring
Powerful visualization and management of your security posture in one unified view
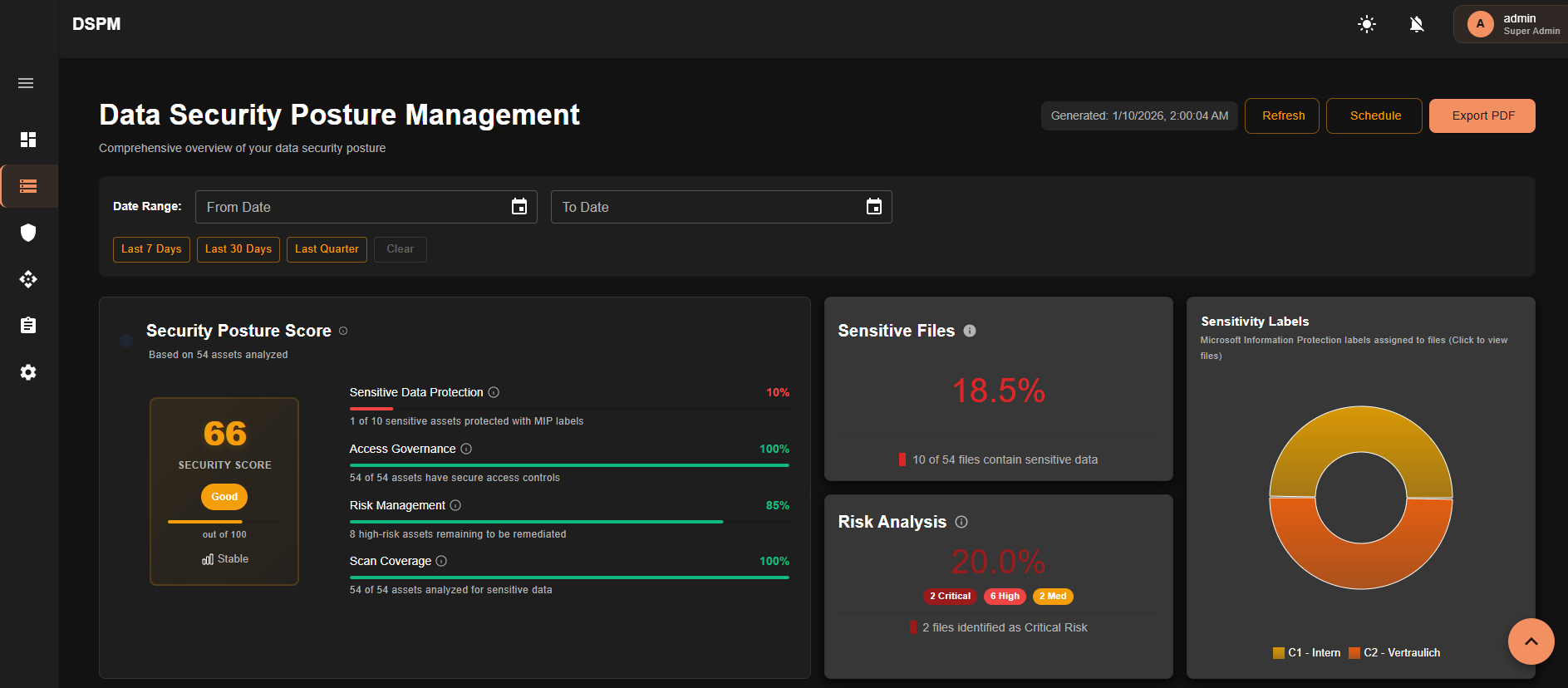
Track your organization's overall security posture with real-time scoring and trend analysis
Identify and monitor files containing sensitive data across your infrastructure
Visualize critical, high, and medium risk assets with actionable insights
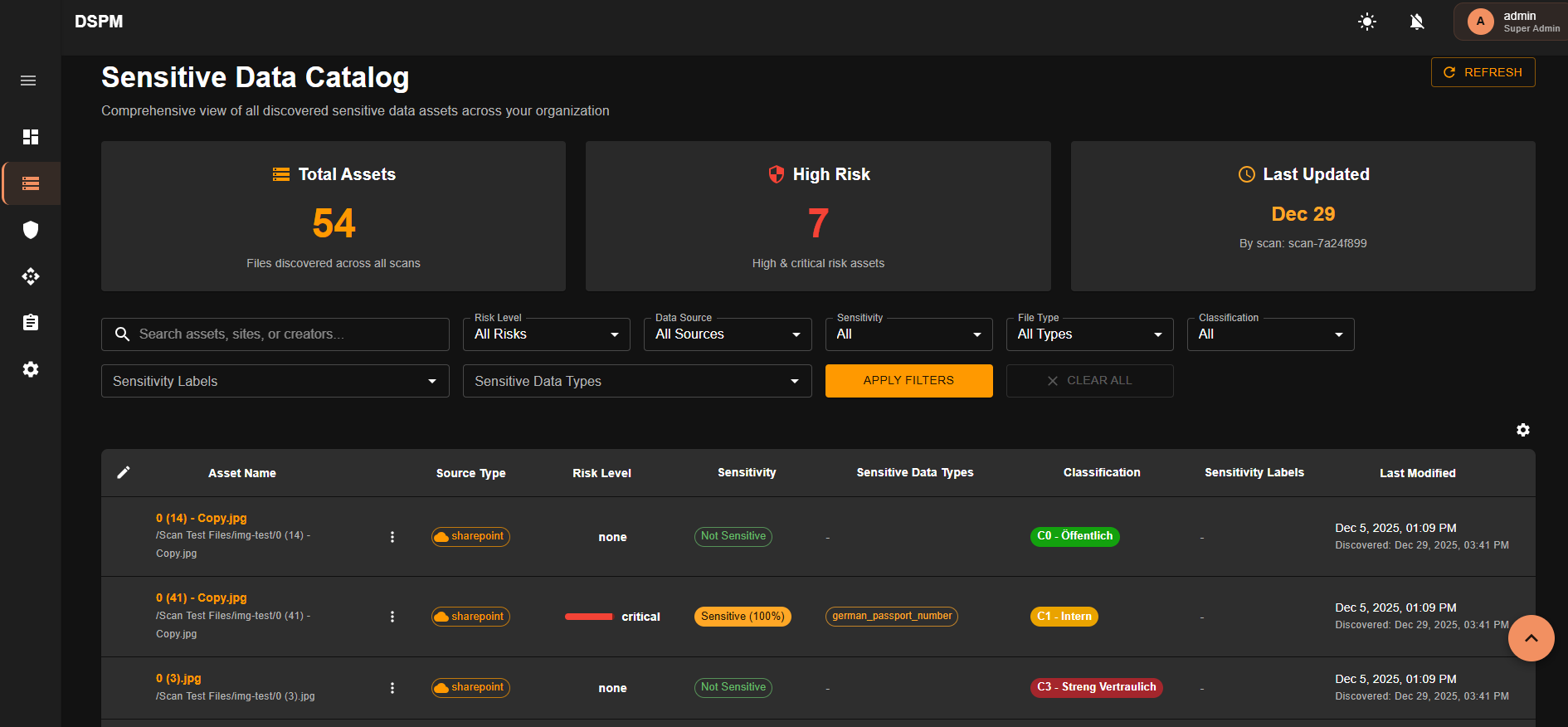
Browse all discovered sensitive data assets with detailed metadata and classification
Filter by risk level, data source, sensitivity, file type, and classification labels
View Microsoft Information Protection labels and custom classification tags
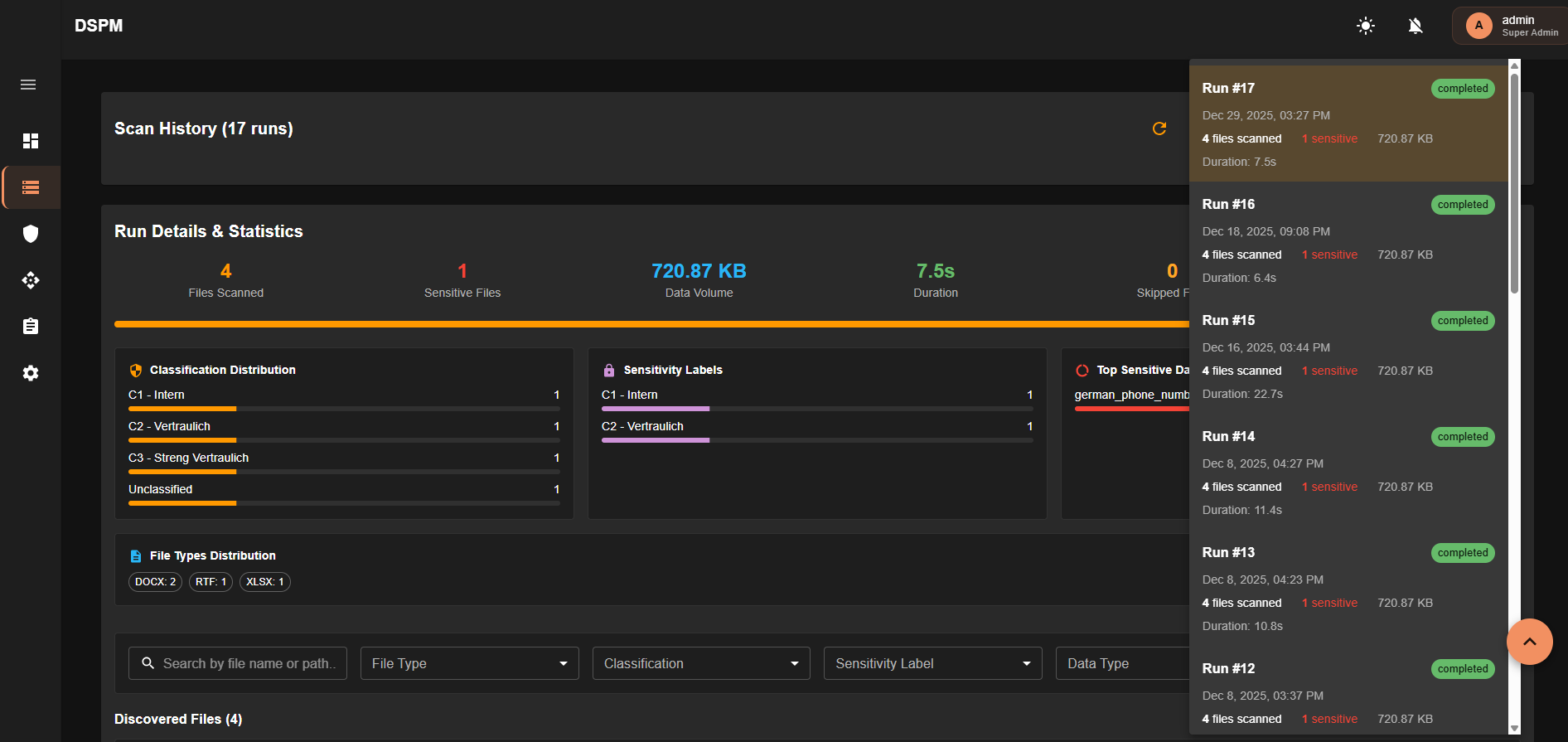
Complete audit trail of all scan runs with timestamps and status information
Detailed metrics on files scanned, sensitive data found, and scan duration
Analyze discovered data types and classification distribution across scans
Trusted by security teams across industries
"The system is very extensive in terms of what it can do. It effectively covers compliance aspects we were concerned about, and the performance is impressive—it's very quick; once you change a setting, it's pretty much immediate. What we really appreciate is that it feels intuitive and simple in its structure."
Explore whitepapers and case studies on Data Security Posture Management
Learn how CyberTide's DSPM solution provides comprehensive visibility, continuous monitoring, and proactive security management for your organization's data assets.
Discover how organizations are transforming their data security approach with CyberTide's DSPM and Data Classification solutions for comprehensive visibility and protection.
Join leading organizations in strengthening their data security posture